Frequently Asked Questions (FAQ's)
Security Camera System
IP stands for Internet Protocol. An IP camera is a digital video system that can transmit data over a network. These systems work with mobile devices so that you can view your security feed from anywhere with an Internet connection. IP cameras may also be referred to as network cameras or webcams.
In a traditional security system, data is transmitted through a cable to a DVR (digital video recorder). With an IP camera, the Internet is used to transmit digital video. The unit contains everything it needs to do this. It’s connected to your network much like other external IT equipment like a printer. To store video, your IP camera may contain storage in-unit or it may transmit video to a device also connected to the network to be stored, also known as a network video recorder (NVR). Digital cameras and IP cameras capture images the same way, although the transmission method is different. Your quality won’t be compromised with an IP camera—in fact, the resolution is better.
You can use either a physical router for your network (wired) or a WiFi connection (wireless). Wired networks tend to be more secure and reliable, although WiFi is easier, it leads to the increased need for security. Surveillance Secure can help you encrypt these networks and customize a wireless network to minimize chances of any problems with a WiFi setup. You may also choose to use a cellular network, which tends to be safer than WiFi, but also slower. Surveillance Secure can discuss your options with you to determine which one would be best for your custom setup and security needs.
Closed circuit television (CCTV) cameras are a traditional analog system of using cameras that use a DVR to record video. They’re reliable, relatively inexpensive, and easy to install. However, they don’t offer you the same versatility, high resolution, and higher security that IP cameras do.
For an IP surveillance system, you’ll need the actual IP cameras, an NVR or other type of storage system, accessories such as a microphones and speakers generally will come built into the cameras so additional parts will not be required. At Surveillance Secure, we can help determine your needs and set you up with the best equipment for your budget.
IP surveillance systems offer you many advantages that traditional CCTV systems don’t. They offer: · Higher resolution · Easy install · Improved capabilities for the cost · Faster and more reliable · Easy to manage · Easy to meet IT compliance regulations · And more!
DVR stands for Digital Video Recorder. A Security DVR is a device that takes the video from analog cameras and converts it to digital format to be recorded on a hard drive. HD video can be recorded. These devices can go weeks or even months with no maintenance.
NVR stands for Network Video Recorder. This type of recorder is used only with digital cameras (IP cameras). It functions the same as DVR.
A video capture card, or DVR card, is the graphics card inside a DVR system that is used to capture the video feed and store it on the hard drive.
There are a number of factors that come into play. How many cameras are in the system? At what framerate (FPS) is the video being recorded? What size hard drive does the DVR/NVR have? Our preconfigured systems usually provide several weeks of archive when set to motion detect mode.
Motion detection is a software-based feature. When pixels in the image change, the software alerts the system to begin recording. You can set the sensitivity on most DVR/NVRs so that drive space isn’t wasted on every stray cat that wanders through the property.
Yes. Onsite monitoring of both live and recorded video is possible.
Yes. All of our Security DVR/NVR systems are Internet enabled. That means you can view live and recorded video from anywhere via an Internet connection.
Basic DSL or cable will suffice in most cases. DSL works for DVRs, but Cable is recommended for NVRs.
Most Internet-enabled Security DVR/NVR systems allow multiple users to view the same site simultaneously. However, as more people look at the same cameras/DVR/NVR at the same time, the bandwidth will be shared between them. This reduces image quality.
Yes. Make sure the Security DVR/NVR system you select comes with an audio option. Most analog cameras do not come with built-in audio, so you will probably need a separate audio kit if you chose analog cameras over digital.
Yes. All of our Security DVR/NVR systems come with this feature. However, an optional audio module is needed to allow you to listen to live and recorded audio from anywhere via the Internet.
This will depend on the size and layout of the area you wish to survey. On average, we recommend one camera per 600 square feet for an Analog System and per 1200 square feet for a Digital System.
Yes. You can use your existing CCTV cameras. We offer a hybrid NVR which gives you the ability to use both Analog and Digital Cameras.
Surveillance Secure carries a large selection of security camera lenses, but the lens you will need depends on where and how you plan to use it, so check with our professionals to learn more and make a good choice.
An auto iris lens provides a consistent video image in areas where light levels vary. This is important for maintaining a viewable stream in both high and low light situations.
Illumination is measured in units called Lux.
Yes, but you need a special camera called a Pan-Tilt-Zoom or PTZ camera. Browse our selection of PTZ cameras, and find the one that is right for you. Or we can make recommendations based on your specific needs.
Most PC-based Security DVR Systems use Windows 10 Professional or above, and Standalone Security DVRs are Linux based.
Use Siamese cable, which is an RG59 coaxial cable and a pair of 18-gauge wire in the same jacket, to make installation easy for Analog Cameras. Use Cat 5 or 6 for IP cameras
Security DVR/NVRs will come back on as soon as power is restored. However, we suggest an uninterruptable power supply (UPS) which provides a short period of backup power and also serves as a surge protection device. This ensures your video surveillance will still be online in the event someone cuts the power to break in unnoticed.
Our Security systems work with most PC-based and electronic cash registers. Contact us with the make and model of your register, and we can tell you if your system is compatible.
Yes. If the alarm is triggered, the DVR/NVR/IP Camera can reach out to a monitoring service.
Smart Home System
1) Quick blink: The device is in configuration mode (SmartConfig™) and waiting for setup. This mode is enabled after the device is powered on for first time or you long press the reset button.
2) Blink every sec.: The device configuration is failed. This is usually caused by incorrect input of password. Please reset the device and try again.
3) Slow blink for 4 times and stop for 1 sec. and repeats the cycle: The device is in AP configuration mode. This mode is enabled after you long press the reset button when the device is already in configuration mode.
4) Off: The device is configured successfully. You can view the device shortcut icon in the main control page or tap the “+” icon on top right corner and then choose “Device list” to view the device.
1) Make sure your smartphone is connected to your Wi-Fi network;
2) Switch the device to configuration mode (refer to FAQ 1-1);
3) Open the app, tap the “+” icon on top right corner and then choose “Add device”;
4) In the configuration page, the Wi-Fi SSID should be filled automatically and you just need to input the password of your Wi-Fi network to start the configuration.
Note: The password of your Wi-Fi network will be saved and you will never need to input the password the next time when you configure the devices.
1) Make sure Wi-Fi (WLAN) is enabled on your smartphone and your device is in AP configuration mode (refer to FAQ 1-3);
2) Open the app, tap the “+” icon on top right corner and then choose “Add device”;
3) In the configuration page, tap “AP mode” on top right corner and tap “OK” after you read the prompt. The app will lead you to the Wi-Fi selection page;
4) Connect to the network “BroadlinkProv” and tap to return. The app will show a Wi-Fi list. Please designate the same Wi-Fi network you used before AP configuration and input the password;
5) After configuration, the app will automatically connect to your previous Wi-Fi network and you will see the device in the list.
Note:When using AP configuration, your smartphone should connect to the same Wi-Fi network that you want the devices to connect to.
For smart plugs, please long press the ON/OFF button to reset the device. For universal remote and other devices without ON/OFF button, use pins to hold the reset button until the Wi-Fi indicator starts quick blink.
Our products currently only support 2.4G Wi-Fi network and do not support 5G network.
In the main control page, tap “+” on top right corner and choose “Device list” to view all devices. For iOS system, slide from right to left on a device item to delete it; For Android system, long press the device icon and choose “Delete” to delete the device.
Note: Deleting shortcuts will not actually delete the device from list.
You can modify the default device name in either ways:
1) Long press the device item on the device list and choose “Edit name” from popup menu.
2) In the device operation page, tap the icon on top right corner and choose “Edit device”.
You can backup all device and APP settings to cloud and restore it when you use a new smartphone. You need to login with your account before backup operation.
To backup settings: Tap the icon in top left corner and then choose “Backup” in the menu. Tap “Backup to cloud” and choose “OK” to start backup.
To restore settings: Tap the icon in top left corner and then choose “Backup” in the menu. Tap “Cloud backup list” and choose a backup file from the list to start restoration.
Note: After restoration, you need to connect your devices in the same Wi-Fi (WLAN) network before remote control.
You can share the settings to other phones in the same Wi-Fi (WLAN) network without using account. To use this function, the shared phones and importing phones should have the same version of APP.
Tap the icon in top left corner and then choose “Share” in the menu. Tap “Share to other phones in WLAN” to prepare the sharing.
On another phone, tap “Import from shared phone in WLAN” in “Share” menu, the APP will search available sharing data and import it.
Note: Please keep your phone active (unlock) during sharing and importing.
You can use cloud share function to share your RM panel to the cloud. Other users can download the shared panel and do not need to learn each button.
Only who connected to your Wi-Fi network is able to find your device. Set a complex password for your Wi-Fi network and keep it confidential will help to prevent intrusion. To keep privacy from other users in the same network, you can lock the device and other users will never find the device even they are in the same network. To lock the device: Tap the icon on top right corner and choose “Device info”. Tap “Lock the device” to lock your device.
To make sure your devices are not controlled by any unauthorized users before you re-configure them using another smartphone, you can:
1) Power off all devices; or
2) Reset all device.
Please check if you have deleted the files under BroadLink directory (for Android phones it is stored in the root directory of SD card) including pictures or changed the SD card. If you have done the above operations by mistake, please uninstall the APP and completely delete the folder and then reinstall the APP.
Note: You do not need to configure again after reinstallation of APP. The devices can be found automatically when you connect to the same Wi-Fi network which you used previously.
You can use one of the two methods to add a remote:
1) On main control page, tap “+” on top right corner, select “Add remote” and choose a remote type. (you need to select an RM device before choosing remote type if you have more than one RM device);
2) On main control page, tap “+” on top right corner and select “Device list”. You can select an RM device and choose a remote type from the list. (If you have added remotes before, you need to tap “…” on top right corner of remote list and choose a new remote type to add).
Note: For the first version e-Control APP, user can find a black semicircle icon on the left side when adding template for the first time. Tap the icon to pop up the sidebar and tap “Add” in the bottom to add a new template.
In the device panel, tap an unlearned button, a prompt box including “waiting for button learning” will pop up and the orange LED of the device will be on. Point the remote to RM and press the matching button on remote. If the orange LED is off and it shows “Save Successfully”, it means the learning is successful. Then you can tap the learned button on APP, if the orange LED is on, which means the IR command is sent successfully.
When you add a remote, please choose “Air Conditioner”. A prompt box will pop up and the orange LED will be on. Then press any button of “ON/OFF” / “Mode” / “Temperature up and down” and the orange indicator will be off. The device will search the IR code in the cloud code library and download the matched template. After the template is downloaded, you can start to use all functions without further learning.
When you download the pre-defined aircon panel from cloud, the template may not 100% match your model. Please try to learn more buttons to select a more suitable template. If you still cannot get an exact same template from cloud, please try to add a user-defined aircon and learn each button. Please also contact our customer service (https://intl@broadlink.com.cn%29/ to submit the model of your aircon. We will update the code on our cloud as soon as possible.
The IR code of aircon is more complex than TV. Each button of TV remote only represents a specific IR code. Each button of aircon may trigger a code combination, including temperature, mode, wind speed, etc. So we pre-define buttons for frequently used functions, such as cooling, heating and auto mode. Each of them are treated as ON button for a combination. For example, if you want to learn cooling at 22°C, you should pre-set the mode to cooling and temperature to 22°C on your remote and then press the ON/OFF button to turn off the aircon. Tap “Cooling at XX°C” in the panel on APP to prepare learning. Now, press ON/OFF button on the remote control to finish the learning and the learned status will be “turn on cooling at 22°C”. You can learn the OFF button in any status when you press the ON/OFF button to turn off the aircon (Although we use only one button for both ON and OFF functions on aircon remote but in the APP you need to learn them separately.)
You can repeat the above learning steps to learn all the status with all temperature levels.
Choose an unlearned user-defined button and tap “Learn combo” to start the learning. Combination button learning can execute multiple commands. For example, if you want to switch to Channel 128 for TV, you need to learn button “1”, “2” and “8” one by one. When you tap the button CH128, it will execute the command 1-2-8, just like you press the buttons 1, 2 and 8 on remote. You can also learn a combination button to turn on set-top box, TV and audio just by pressing one button.
These two panels are preset with all IR codes for “mi TV” and “Apple TV” which can be used by users directly without learning.
By creating a scene, you can tap once to activate all selected devices with preset time lag. You can select devices and define the action of each device.
Long press the learned button on the panel and tap “Timer ON”. After setting, tap “Save” on top right corner to save the timer.
Max 15 timer tasks be added for RM.
On remote list page, tap “…” on top right corner and select “Timer”. You can view and delete the timers here.
Powered by BroadLink Cloud service, users can remotely control their devices via external networks (3G/4G/other WLAN) even they are not at home.
The Android APP version above 3.4.9 and iOS APP version above 2.4.7 improved the performance of remote control from external networks. However, users are required to setup the correct region and also update the product firmware, otherwise remote control from external networks may be not available.
Please download the service accouchement file to learn how to update APP and firmware to support this feature:
http://www.ibroadlink.com/en/app_update.pdf
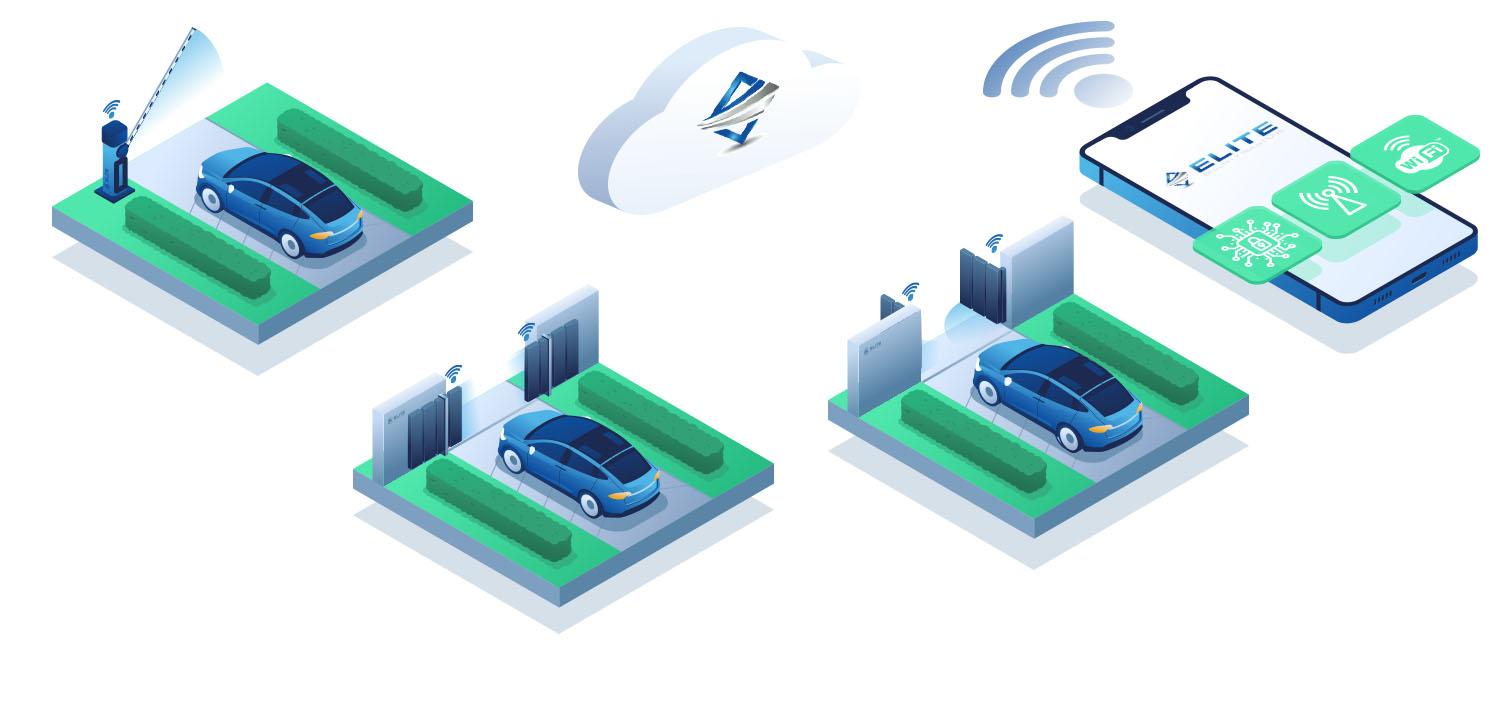
Access Control System
Access control can be applied to both physical security solutions as well as logical ones. The access control system permits only authorized personnel to enter the building or system. The system does this with a password protection system or for a physical system, a key card or fob is utilized. These fobs can be controlled remotely to be activated or deactivated.
Access control provides a range of solutions to businesses that need to control who accesses their systems. They provide added security from physical keys, although you will still be able to utilize physical keys should you need to do so. Electronic keys are virtually impossible to replicate and you won’t have to worry about losing your keys as every key is programmed with a unique code that can be replicated by the provider if lost or stolen. Your old key will then be deactivated and rendered useless.
Another benefit of access control systems is that you’ll be able to set days and times that each user is able to access the building and even customize locations that your employees can access. Access control makes security easy and customizable for everyone that needs to be on site.
You’ll also be able to record who accessed your building and when. All of this data is recorded and you’ll be able to access it at any time. This data is particularly useful for times when security breaches, theft, or other suspicious activity occurs.
For an IP surveillance system, you’ll need the actual IP cameras, an NVR or other type of storage system, accessories such as a microphones and speakers generally will come built into the cameras so additional parts will not be required. At Surveillance Secure, we can help determine your needs and set you up with the best equipment for your budget.
Access control systems begin with a consultation with us at Surveillance Secure. Hardware will be needed for physical access systems, including card or fob readers, door switches, and a control panel. The control panel is integral to the system and controls all the different access points of the building. Access control systems are versatile and can grow with your business, so if you need a bigger system, simply integrate a new control panel.
The server of the system will have all the users in a database, which allows for customization of access times and locations. When the card is introduced to the reader, a frequency is read by the controller and the user is verified through the database. If verified, the door will unlock. If not, the controller registers the breach and the proper monitors will be notified.
Yes, as systems have battery backup plans for emergencies to keep the access control system functioning. If the power is out for longer than the battery backup can accommodate, this is a situation in which you would need to utilize physical keys.
No, access control systems are extremely versatile and can work on a variety of entries and exits such as elevators, gates, parking restrictions, vehicles, and garage doors.
Burglar Alarm System
A Security Home Alarm is a system designed to detect intrusion – unauthorized entry – into a building or area. Security alarms are used in residential, commercial, industrial, and military properties for protection against burglary(theft) or property damage, as well as personal protection against intruders. GPS trackers & car alarms likewise protect vehicles and their contents. Everyone should have alarms
Some alarm systems serve a single purpose of burglary protection; combination systems provide both fire and intrusion protection. Intrusion alarm systems may also be combined with closed circuit television surveillance systems to automatically record the activities of intruders, and may interface to access control system for electrically locked doors. Systems range from small, self-contained noisemakers, to complicated, multi-area systems with computer monitoring and control.
Design
The most basic alarm consists of one or more sensors to detect intruders, and an alerting device to indicate the intrusion. However, a typical premises security alarm employs the following components:
Premises control unit(PCU), or panel: The "Brain" of the system, it reads sensor inputs, tracks arm/disarm status, and signals intrusions. In modern systems, this is typically one or more computer circuit boards inside a metal enclosure, along with a power supply.
Sensors: Devices which detect intrusions. Sensors may placed at the perimeter of the protected area, within it, or both. Sensors can detect intruders by a variety of methods, such as monitoring doors and windows for opening, or by monitoring unoccupied interiors for motions, sound, vibration, or other disturbances.
Alerting devices: These indicate an alarm condition. Most commonly, these are bells, sirens, and/or flashing lights. Alerting devices serve the dual purposes of warning occupants of intrusion, and potentially scaring off burglars.
Keypads: Small devices, typically wall-mounted, which function as the human machine interface to the system. In addition to buttons, keypads typically feature indicator lights, a small mulch-character display, or both.
Interconnections between components. This may consist of direct wiring to the control unit, or wireless links with local power supplies.
Security devices: Devices to detect thieves such as spotlights, cameras & lasers.
In addition to the system itself, security alarms are often coupled with a monitoring service. In the event of an alarm, the premises control unit contacts a central monitoring station. Operators at the station see the signal and take appropriate action, such as contacting property owners, notifying police, or dispatching private security forces. Such signals may be transmitted via dedicated alarm circuits, telephone lines, or Internet.
Passive infrared detectors
A passive infrared detectors used to detect motion.
The passive infrared (PIR) motion detector is one of the most common sensors found in household and small business environments. It offers affordable and reliable functionality. The term passive refers to the fact that the detector does not generate or radiate its own energy; it works entirely by detecting the heat energy given off by other objects.
Strictly speaking, PIR sensors do not detect motion; rather, they detect abrupt changes in temperature at a given point. As an intruder walks in front of the sensor, the temperature at that point will rise from room temperature to body temperature and then back again. This quick change triggers the detection.
PIR sensors may be designed to be wall or ceiling mounted, and come in various fields of view, from narrow "point" detectors to 360 degree fields. PIRs require a power supply in addition to the detection signaling circuit.
Microwave detectors
This device emits microwaves from a transmitter and detects any reflected microwaves or reduction in beam intensity using a receiver. The transmitter and receiver are usually combined inside a single housing (monostatic) for indoor applications, and separate housings (bistatic) for outdoor applications. To reduce false alarms this type of detector is usually combined with a passive infrared detector or "Dualtec" alarm.Microwave detectors respond to a doppler shift in the frequency of the reflected energy, by a phase shift, or by a sudden reduction of the level of received energy. Any of these effects may indicate motion of an intruder.
Photo-electric beams
Photoelectric beam systems detect the presence of an intruder by transmitting visible or infrared light beams across an area, where these beams may be obstructed. To improve the detection surface area, the beams are often employed in stacks of two or more. However, if an intruder is aware of the technology's presence, it can be avoided. The technology can be an effective long-range detection system, if installed in stacks of three or more where the transmitters and receivers are staggered to create a fence-like barrier. Systems are available for both internal and external applications. To prevent a clandestine attack using a secondary light source being used to hold the detector in a 'sealed' condition whilst an intruder passes through, most systems use and detect a modulated light source.
Glass break detection
The glass break sensor may be used for internal perimeter building protection. Glass break acoustic detectors are mounted in close proximity to the glass panes and listen for sound frequencies associated with glass breaking.
Seismic glass break detectors, generally referred to as "shock sensors" are different in that they are installed on the glass pane. When glass breaks it produces specific shock frequencies which travel through the glass and often through the window frame and the surrounding walls and ceiling. Typically, the most intense frequencies generated are between 3 and 5 kHz, depending on the type of glass and the presence of a plastic interlayer. Seismic glass break detectors “feel” these shock frequencies and in turn generate an alarm condition.
Window foil is a less sophisticated, mostly outdated, detection method that involves gluing a thin strip of conducting foil on the inside of the glass and putting low-power electrical current through it. Breaking the glass is practically guaranteed to tear the foil and break the circuit.
Smoke, heat, and carbon monoxide detectors
Heat detection system
Most systems may also be equipped with smoke, heat, and/or carbon monoxide detectors. These are also known as 24 hour zones (which are on at all times). Smoke detectors and heat detectors protect from the risk of fire and carbon monoxide detectors protect from the risk of carbon monoxide. Although an intruder alarm panel may also have these detectors connected, it may not meet all the local fire code requirements of a fire alarm system.
Traditional smoke detectors are technically ionization smoke detectors which "create an electric current between two metal plates, which sound an alarm when disrupted by smoke entering the chamber. Ionization smoke alarms can quickly detect the small amounts of smoke produced by fast flaming fires, such as cooking fires or fires fueled by paper or flammable liquids." A newer, and perhaps safer type is a Photoelectric smoke detector. It contains a light source in a light-sensitive electric sensor, which is positioned at a 90-degree angles to the sensor. "Normally, light from the light source shoots straight across and misses the sensor. When smoke enters the chamber, it scatters the light, which then hits the sensor and triggers the alarm. Photoelectric smoke detectors typically respond faster to a fire in its early, smoldering stage – before the source of the fire bursts into flames."
Vibration (shaker) or inertia sensors
Strain-sensor cable installed on a chain-link/barbed-wire fence
These devices are mounted on barriers and are used primarily to detect an attack on the structure itself. The technology relies on an unstable mechanical configuration that forms part of the electrical circuit. When movement or vibration occurs, the unstable portion of the circuit moves and breaks the current flow, which produces an alarm. The technology of the devices varies and can be sensitive to different levels of vibration. The medium transmitting the vibration must be correctly selected for the specific sensor as they are best suited to different types of structures and configurations.
A rather new and unproven type of sensors use piezo-electric components rather than mechanical circuits, which can be tuned to be extremely sensitive to vibration.
pros: Very reliable sensors, low false alarm rate and middle place in the price range.
cons: Must be fence mounted. The rather high price deters many customers, but its effectiveness offsets its high price. Piezo-electric sensors are a new technology with an unproven record as opposed to the mechanical sensor which in some cases has a field record in excess of 20 years.
Passive magnetic field detection
This buried security system is based on the Magnetic Anomaly Detection principle of operation. The system uses an electromagnetic field generator powered by two wires running in parallel. Both wires run along the perimeter and are usually installed about 5"/12cm apart on top of a wall or about 12"/30cm below ground. The wires are connected to a signal processor which analyzes any change in the magnetic field.
This kind of buried security system sensor cable could be embedded in the top of almost any kind of wall to provide a regular wall detection ability, or can be buried in the ground. They provide a very low false alarm rate, and have a very high chance of detecting real burglars. However, they cannot be installed near high voltage lines, or radar transmitters
The difference between fixed code (PT2262) and learning code (Ev1527)
Nowadays many people are afford to get a burglar alarm system for their home and business. Make decision on purchasing burglar alarm system, some people may not understand what the fixed code is for alarm system or what the learning code is.
What’s the difference between fixed code and learning code? Which one is better?
Fix Code:
IC: Encode chip PT2262 (Traditional wireless detectors)Decode chip PT2272 (Traditional wireless alarm control panel)Address: 3 to the 8th power (6561 unique addresses).
Features:
1.Security level not high, few addresses may cause duplicate address code. This may cause false alarm.
2.It’s very difficult to increase (add) extra wireless detectors or sensors for user. The theory of fixed code is that the address of detectors (encode) must match the address of alarm control panel (decode). If want to increase the detector, you need to know the alarm control panel address. By the way, encode address need user to have some basic knowledge of electronic technology.
3.It’s a terrible thing, if lost the remote controller (keyfob). Because alarm control panel can not delete the address (or detectors), people pick up the remote controller can freely control your alarm system; If ask user to change the address of alarm system, that’s troublesome, you may need to set all the wireless detectors and sensors, as well as detectors match the new address of control panel.
Learning Code:
IC: eV1527Decode: MCUAddress: 2 to the 20th power
Features:
1.High security level, 100 million addresses decrease the duplicate address rate.
2.It’s easy and convenient to add and delete the wireless sensors and detectors. All the wireless detectors and accessories using different address code, you just need to learn them into alarm system.
Don’t worry when you lost the remote controller (keypad), you just need to delete it from alarm control panel, then that remote controller is not able to communicate with alarm control panel, and it’s useless, can not control the alarm system any more.
Rolling Code
This code is widely used in Car Alarm System
Why Should I Buy A Home Security System?
Home Security is not necessarily a subject to be taken lightly. A lot of time and effort is put into investing in a property, building a house, developing the home, designing a home as well as living in a home, however often times presently there isn't enough time and effort dedicated to securing your home. You will need to invest in security actions simply because security protects you and your family members and safeguards your valuables and peace of mind.
Several factors go in to identifying how protected your house will certainly end up being. Many people assume that through locking their doorways their home is very safe and secured, but the truth is there are many ways which can be just as important as based doors to ensure the secure home. You could be one of the house owners who find security issues confusing as well as end up investing in measures that aren't genuinely effective or befitting their home. In that case, below you will find several helpful home security troubles that you should look into making your home safer.
Let us begin by reviewing some of the low priced issues regarding security. As you set out to increase your home or office's security, make sure you are engaging in the burglars head. Burglars really want to take the most within the shortest amount of time while using least amount of threat. To prevent this from occurring there are several steps you can take to interrupt their particular flow.
* Utilize motion detectors for you to switch on the outdoor lighting as well as light up the region adjoining your home.
* Make sure gates and windows are generally visible from a long distance by eliminating or perhaps trimming shrubbery along with trees.
Such things can offer a cover or even place to cover for thieves.
* When traveling out of the neighborhood, make plans regarding garden care and get a good friend or perhaps a neighbor to get the mail along with newspapers. Also, utilize timers to mimic the particular lighting pattern associated with an occupied home.
* Make sure you possess good window as well as door locks (including deadbolts) to stop or even slow don the thief.
Many times, the aforementioned solutions will steer thieves away from your home. However, sometimes the actual burglar will be persistent. Persistent intruders should be frightened off much more by loud sounds from the guard dog as well as an burglar alarm. If you have zero interest in obtaining a dog, think about a home alarm system simply because they function much more proficiently.
Burglar alarm systems might be either simple products or complex units. Prices vary tremendously dependent on their own sophistication. It is usually highly preferred you ought to invest in a much more sophisticated home security system should your home has a lot of valuables or is within a neighborhood noted for frequent burglaries because intruders may without difficulty turn off simple systems. Of course, it's the unfortunate truth of the matter that just about all security can be compromised or evaded, however high-quality systems make it extremely tough for the most smart thieves.
House Alarm System Guidelines
* Search for a burglar alarm system that incorporates a method to initiate a burglar alarm manually if perhaps you actually suspect a intruder. This is a good method to scare someone regarding if you notice peculiar disturbances and so are not sure where they're coming from.
* Put your alarm system key pad within more than one area. Most people position the keypad at the front as well as the back door of their home. You should also possess a second keypad installed in your master bedroom as well as the office. Some approaches utilize a dual technique that involves a pair of different disabling components.
* Contemplate merging your alarm system together with security doors along with motion detectors using noises, lasers, as well as infrared detectors.
How to select the correct security system for home safety?
When talking about home security, there are lots of aspects need to concern, people usually is concerned on buying home security system, that’s true, these professional high tech equipment can help you a lot.
Home safety tips are as important as installation of home security systems
Even you have installed high tech alarm system. If you forget to Arm the system then it’s useless. It’s just like you forget to lock the door, so home safety and security tips are very important than just install a set of alarm system.
When install security system? Need it or not?
If you are in the high crime rate places or experienced the burglary before, or heard your neighbors robbed recently, you will think about home security and install alarm system. What I’m thoughts are it’s better to be prepared in case of bad thing happen, the theory like the each commercial building need to install fire alarm system. If buildings catch the fire, then the loss will be huge.
Self-monitoring or 24 hours monitoring alarm system?
Due to economic crises around the world, less people can afford monthly fees for monitoring their homes. Now more and more people are using self-monitoring alarm system, even some monitoring companies provide free installation service and equipment.
What’s 24 hours monitoring?
Companies that setup central monitoring station provide 24 hours monitoring service to home owners or business. They play the role of the link between your home and police station (other authorization department). The alarm will be handled by trained operator. Home owner need to sign the contract and pay monthly fees for the service.
The benefit for monitoring service is you gave the monitoring work to trained and professional operators, no need to handle the alarm or emergency by yourself. These trained operate are better than you on handling these events.
What’s self-monitoring?
Self-monitoring means you will get informed when the abnormal event triggered the alarm, rather than go to central monitoring station, you will be replace the role of operators to handle the alarm by yourself, and be the link between your home and police station (or other authorities department).
The advantages of self-monitoring are you get informed immediately, and you check out what’s happen in your home or property and business. You only need to pay the cost of equipment, you don’t even to pay for the installation, due to most of these alarm systems are do it yourself to cut the cost.
Alarm system or video surveillance system?
Due to the privacy issue, the video surveillance system can install outside of house for perimeter surveillance, or inside of exit and entrance of house.
Video surveillance systems are suitable for the villa, cottage, and individual house. When choose video surveillance system, you may need hire security guard to monitoring in real-time, handle and report the abnormal events. Without security guard, surveillance systems only provide the evidence (video) after unhappy things happen. By the way, if you want to get the useful evidence, it’s better to choose high definition (resolution) equipment.
Home alarm systems are widely used; you may find it in your neighbor’s house. It’s suitable for small apartment, from house to villa, even the bank vault. The beauty of alarm system is they will not invade the privacy when providing the effective protection, also with low cost, affordable price. In addition, use the wireless alarm system; you may no need to hire somebody to do the installation construction works.
Wireless alarm system or hardwired alarm system?
Wireless means no need to run cables, and no need to do lot of big scale construction work when you install wireless alarm. Also you can remove and re-install it to your new house when you move out from old house.
Lotof people trust on hardwired alarm systems because they are more reliable than wireless one. Hardwired alarms run the cables between vary of detectors and alarm panel. If you have unfinished house, or re-decoration on the house, then hardwired alarm system is the best choice. If you rent a house, or your house are already decorated, then you should take the consideration of wireless alarm system.
The problem for wireless alarm may come from two aspects; firstly, wireless distance transmission limitation between detectors and alarm panel, secondly, wireless alarm detectors run on battery, It may require you do more maintenance and testing frequently than hardwired alarms.
The other concern is the cost. The cost on the equipments for wireless alarm and hardwired alarm are the same. On installation, wireless cost less, hardwired need to pay more on cables and construction works.
Commonly used detectors for alarm system:
Different detectors are with different function and detection ability. Choosing the best detector to meet the specific application is very important.
PIR-based Motion Detector: Suitable for the indoor movement detection that without pets.
Dual Tech (PIR + Microwave) Motion Detector: Indoor type is suitable for indoor usage. The dual tech motion detector usually is with pet immune feature. Outdoor type is with waterproof and special anti-interference design for outdoor usage.
Magnetic Contact Switch: The widely used sensing close and open device for windows and doors.
Mechanic based vibration detector: Mechanic vibration detector is sued in vibration detection application, suitable for the mechanic vibration for ATM machine, safes, and walls of vault.
Acoustic based vibration detector: Due to false rate, we seldom recommend this detector for detection of vibration. It’s so sensitive to noise, not vibration itself. Huge noise thunder at summer weather, car horn…etc may trigger the detector.
Glass break detector: They are professional devices on protecting of glass windows. It will analysis the noise to reduce the false alarm. I mean the true glass break detector, not the cheap one that only with acoustic vibration detection, without noise analysis. The cheap one work as the same as acoustic based vibration detector, many false alarms, it’s useless.
Importance items that you should not omit when install alarm system
Except commonly used intrusion detection detectors and control accessories, you may need to consider other importance detectors and equipments.
Many people are thinking about the burglary, and forget the fire alarm. As we know, all the burglar alarm system with fire alarm detection features. It’s better to order 2 units or more smoke detector, heat detector for your system.
More over, a panic button installed in your bedroom is very important to your home security.
How to Install a Home Alarm System
A home alarm system can protect you and your family as well as your home and belongings in the event of a burglary. Some home alarm systems are complex and requires professional installation, while others are easier installed. This page takes you through the general steps of how to install a home alarm system. Specific instructions will differ based on the alarm that you have chosen.
Introduction
There are three general types of home alarm systems: a local home alarm, which sets off a local sound alarm in the case of a burglary, an auto-dial system which dials programmed numbers, such as 911, in the case of an emergency, and a monitored home alarm system, which is monitored by an agency. The functions of the monitored alarm system differ, but usually include the ability for the company to contact you if the alarm goes off and dispatch private security agents to your home. Most monitored home alarm systems will be installed by a professional. Regardless of the system, it's best to hire a professional to install your alarm system if you are not familiar with electrical installations, in order to avoid injuries and mistakes during the installation.
Step 1: Understanding
Before installing the alarm system, make sure you understand how it works.
Home alarm systems operate on the functions of a closed circuit electrical system. Voltage flows through the system until it's disrupted, (opened), causing an alarm to set off. Monitors are installed on windows and doors. When the monitors set off, for example when a door is opened, the circuit opens and the alarm rings.
Monitored alarm systems contact the monitoring agency when the alarm sets off. They are connected to a phone or cable. They are activated when you enter the door and you have a limited time to put in a password before the alarm goes off.
Step 2: Planning
After understanding how the system works, it's time to plan the installation. Select the locations of the different components of the alarm system before starting the installation.
A simple alarm system consists of a main control board, sensors, a control panel and a siren.
The main control board controls the alarm system.
The siren should be located at a place where it's easily heard, but not easily found. This way, the alarm will be noisy, but the burglars cannot easily destroy it.
The control panel is the remote control of the alarm and allows you to disarm, disconnect and activate the alarm. it should be located near the front door for easy access. Don't install it so that burglars can see it through the windows.
Sensors are placed on doors and windows.
Many alarm system includes additional functions.
Step 3: Installation
Read the instructions of the specific alarm before starting the installation. Be aware that many alarm systems will require professional installation. If you are not familiar with electrical installations, contact a professional. The best order for installation may vary depending on the alarm. These are the installations steps.
Install the siren.
Install the main control board.
Install window sensors and door sensors.
Install the remote control panel.
Test the remote control panel and each sensor.
Set a password for the remote control panel.
Conclusion
· A home alarm system can allow you to sleep better at night, whether in your home or at vacation, since it provides protection for you, your family and your home and belongings. Before installing a system, make sure you understand how it works and how to install it. Some may require professional installation, but others can be installed if you are familiar with electrical installations.
Video Door Phone System
The IP Door Phone system identifies the user and enables him to access in different ways: by bringing an NFC tag close to the external unit (it can be a card or a smartphone), by showing a QR code to the external unit camera, by associating the smartphone bluetooh and enabling a door opener button or via facial recognition.
No. A user can also have multiple codes / credentials that activate different actions (open the door, deactivate the alarm, etc.). This is useful in families as parents can generate multiple codes for different functions and provide children with only those they deem appropriate.
IP Door phone was also designed for those who want to give independent access to occasional users, only in certain time slots. Just simply create temporary credentials (such as a QR code) valid only for a certain time.
Yes. You can set the IP Door Phone to activate specific actions in combination with your access (simultaneous opening of multiple gates, switching on of the house lights, deactivation of the anti-theft system, etc.).
Gate Automation System
The four prime reasons that home owners install electric gates are:
Security
Convenience
Safety & Comfort
Resale Value
Firstly, security
With increasing 'yob' culture in many areas of the country, more and more home owners are looking to increase the security of their property to combat the opportunist, the hawker, the car thief and the vandal. Automatic and electrically controlled security gates, in conjunction with a video or audio intercom, can enable home owners to provide a secure perimeter and control who has access to the entrance of their property from the safety of the home, home office or even any part of the world!
Secondly, convenience
There are thousands of properties that have wooden or iron gates installed but, incredibly, are permanently left open. The fact is that an open gate is not a gate! However, when you consider the number of times people drive in and out of their homes every day, it probably isn't surprising that they are left open as this avoids the hassle of having to opening and closing them manually, especially when it is cold, windy or raining. Automatic gates will provide the security that people are looking for and no matter what the weather condition, at the press of a button on a small remote control device from inside the warmth of your car or from inside your house, the gate will automatically open and shut safely behind the people your have decided to invite into your home.
Thirdly, safety and comfort
With increasing road traffic, home owners are understandably concerned about the safety of their children and pets and how to stop them wondering out onto busy roads. With an electric gate system, this not only provides a secure boundary but also ensures that even when people or cars enter the property, the gates will automatically close to provide a safe and secure environment for both children and family pets.
Fourthly, resale value
When buying a house, it is strange how one aspect of a property can be the deciding factor. Although an increasing number of homes now have automatic electric driveway gates installed, many people still haven't experienced the convenience that this type of entrance system provides. Not every house has one but there is no doubt that the ones that do will stand out from the crowd.
Generally they can be automated but there will be some exceptions. Much will depend on the layout of the overall site and the state of repair of the existing gates, the gate posts, the gate hinges and the gate leaf alignment.
Automating gates is a highly skilled task and requires a range of skills that generally only gate automation professionals have. Some of the critical tasks include the geometry of the automation, the wiring and programming of the control panel. A number of other core skills will also be required for most projects including civil (eg groundworks), mechanical (eg welding) and electrical engineering skills.
Many people have bought DIY kits off the internet and have spent days trying to get it to work without success and not being able to get hold of the seller for advice or support. Some have eventually got their project working only to experience accidents as the gates close on vehicles shortly after they thought everything was finally finished! Invariably people who start a DIY automation project end up engaging a professional installer - DIY often proves to be false economy as so much can go wrong.
No. Obviously an inclined driveway can stop gates opening but sometimes there it is possible to install a swing gate that opens away from the property. However, it may be possible to install swing gates that open away from the property although you will need to ensure that the gates do not obstruct the public highway.
The solution that most people with inclined driveways adopt is to install a sliding gate; one that either slides to one side of the entrance or a bi-sliding gate where each gate leave slides to each side of the entrance. Much will depend on the space available at the side of the entrance.
All quality installations will provide home owners with manual release keys and instructions on how to release the automation system in the event of a power failure. Some electric gate systems also come with the option of a battery backup. However, all systems come with a manual release facility that can be used in the event of a power
A loop detector is purely to sense the presence of vehicles. Special loop cable, in the shape of a diamond or a rectangle, is dug into the tarmac, concrete or gravel driveway and connected to a detector in the electric gate system's control panel. The loops detect the presence of a vehicle which can send a command to the gate system. The most common use of loops is to enable free exit such that when a vehicle leaves the premises and drives over a loop, the gate automatically opens and therefore avoids the need for a transmitter or special involvement from the home owner. Loops are also placed at the gate entrance as a safety mechanism that avoids the gates closing on a vehicle if the presence of one is detected by the system.
Although some gate motors will automatically lock in the both the open and closed positions, some motors, notably those operating large gate leaves, are designed not to lock. There are a variety of locking devices can be incorporated into any gate system to maximise the security. There are no specific guidelines but as a rule of thumb any swing gate leaf over 2m would possibly require some form of electric lock. A gate over 2m has a lot of leverage – you wouldn't fit your front door with a lock on the same side as the hinges. There are a variety of electric locks available, one of the most popular being a magnetic lock.
Almost every electric gate system has an intercom, either audio or audio and video, which enables people at the gate to contact the home owner. The intercom will either be hardwired between the gate and the house or will be wireless with either a DECT telephone system or a GSM.
In general, they don't - gates are put in place to provide perimeter security. However, there are a range of intercom systems that will dial a mobile number when the intercom button is pressed at the gate and the system can be programmed so that the owner of the mobile phone, once he or she knows who wants to get in, can press a number on their mobile phone which will open the gate - either partially to allow pedestrian access or fully to let a vehicle enter the property. The mobile phone user could be on the other side of the world but the technology still enables them to control the home entrance system.
Just like every car, every electro-mechanical device will fail at some time in its lifetime. An electric gate system, which is constantly subjected to all the elements, really need a service every 6/12 months. Systems that are serviced will continue to operate for years. Option of AMC if not include in bundle offer